itxsahal
August 22, 2025

The Vastaamo data breach is Finland’s most well-known and notorious data security incident. A major breach occurred at the Finnish psychotherapy clinic Vastaamo in October 2020, allowing hackers to access and steal the private medical records of more than 33,000 people.
Because important security updates were not implemented in a timely manner, the Finnish public sector has also experienced several serious security breaches. The largest breach in Finland’s history occurred in Helsinki City last year.
These occurrences demonstrate how important it is to give security first priority when developing software and managing solutions. At Technogenis, we are dedicated to utilizing cutting edge tools and security best practices to make our projects safe and robust against online attacks. In a nutshell, our Security Specialist Aka describes how site security management is carried out like a pro.
You are well aware of the importance of security updates.
Similar to your car’s regular maintenance, security upgrades are necessary to keep everything functioning properly. These upgrades improve security features, address issues found after distribution, and patch vulnerabilities that hackers could exploit. Systems may become vulnerable if these upgrades are ignored, which could result in data breaches, the loss of private data, and significant harm to one’s finances and reputation.
Alonoe Finland has seen a number of noteworthy security lapses in the last 12 months that have affected both the public and private sectors:
A police inquiry resulted from the December 2024 Valio Data Breach, which exposed the personal information of almost 70,000 people due to unauthorized access to the company’s network. technological Incident at Nordnet (February 2025): A technological problem resulted in users viewing inaccurate account information, which led to a brief suspension of digital services.
Sambla Group Data Security Neglect (March 2025): Sambla Group was fined €950,000 by the Finnish Data Protection Authority for failing to implement sufficient data security measures that allowed third parties to access customers’ loan applications.
These occurrences highlight how crucial it is to have regular security updates and strong data protection procedures. By using cutting-edge tools and following security best practices, let us make protecting our projects from cyber attacks a top priority.
In 2023, the average cost of a data breach was $4.45 million, according to an IBM research. That figure increased to $4.88 million in 2024. For something that could have been avoided, that is a significant cost.
In another example, the 2017 Equifax breach, which affected 147 million people, happened because a known vulnerability was left unpatched. The corporation suffered severe financial and reputational consequences as a result of this error.
We use a shift-left security technique throughout the software development lifecycle to protect our projects. This means that in order to prevent potential security flaws from progressing to production, we implement security procedures to detect and address possible problems early and consistently throughout our development process. “Shifting left” refers to incorporating testing and other processes earlier in the software development cycle in order to identify and address issues quickly and produce more dependable and resilient software.
The following are some advantages of using a shift-left security strategy:
Reducing human error and production problems are two benefits of implementing automated procedures. The ability to run several tests at once increases test coverage and frees up testers to work on other projects.
By allowing DevOps and security teams to collaborate in tandem, shift left security expedites the release process. Because problems may be found and fixed earlier in the development cycle, the program quality is enhanced.
In addition to employing techniques like threat modeling, our approach makes use of tools like the Aikido security platform and Platform.sh Observability Suite.
Platform.sh Observability Suite:
For our security efforts, the Platform.sh Observability Suite is essential.
It helps us proactively manageour systems by offering real-time monitoring and notifications.
We can monitor performance indicators, identify irregularities, and promptly address
possible risks before they become more serious thanks to this package.
Another essential component of our security plan is aikido. An extensive suite of tools for advanced code and cloud vulnerability evaluation and scanning is provided by this all-in-one application security platform.
A methodical technique for locating, evaluating, and resolving any security risks to a system or application is threat modeling. This complements our shift-left security approach. Understanding the assets that need to be safeguarded, figuring out potential attackers and their reasons, and identifying potential attack vectors are all part of it. By developing a model that embodies these components, we assist organizations in anticipating and reducing risks before they materialize.
Early in the development phase, Static Code Analysis (SAST) finds weaknesses in our source code.
Infrastructure Code Scanning (IAS): Guarantees the security of our deployment setups.
Open Source Dependency Scanning (SCA): Looks for known vulnerabilities in third-party libraries.
Surface Monitoring (DAST): Examines the production application for any vulnerabilities.
Malware Detection: Prevents malware from infecting our systems using packages that are not listed in any CVE database.
License and SBOM Compliance: oversees software licenses and makes sure our software supply chain is transparent.
We incorporate security upgrades into our agile continuous development process with ease. This is an example of how we handle it:
Identify: Any vulnerabilities are flagged by ongoing monitoring techniques.
Assess: Our security team ranks the upgrades according to their level of risk.
Develop/mitigate: In the upcoming sprint cycle, developers produce patches or updates.
Monitor: Updated code is put through a rigorous testing process called Pentest, which includes automated security tests.
Deploy: The update is released after testing, frequently using automated workflows.
Monitor: To guarantee the efficacy and stability of the update, the system is continuously observed after deployment.
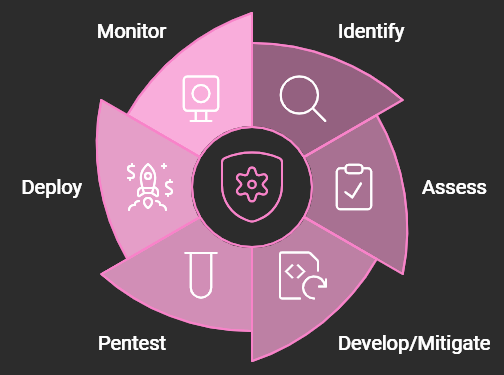
This proactive approach ensures that security is always at the forefront, minimizing risks and maintaining system integrity.
Keeping up with the game
It is essential to stay ahead of potential vulnerabilities by using thorough security solutions and timely security upgrades. To safeguard our projects and guarantee adherence to legal requirements, we consistently invest in cutting-edge instruments and procedures. By doing this, we strengthen our standing as a pioneer in secure application development and solutions management while simultaneously protecting the data of our clients.
Technogenis is your partner in digital growth. We design and develop smart, scalable web and mobile solutions tailored to your business goals. From strategy to execution, we help bring your vision to life through cutting-edge development, SEO, PPC, and more.
SEO & Digital Marketing Agency
Copyright © 2025 – All rights reserved by Technogenis Ltd